
Is your remote desktop secure?
Remote access to company computers or even client computers, known as remote desktop, is a great advantage that increases productivity as it eliminates the need to be physically in front of the computer. This type of access is commonly known as remote desktop, and there are a large number of solutions on the market, although one of the most used, due to its default integration in the Windows operating system, is RDP, which stands for Remote Desktop Protocol.
Remote access follows the logical client-server model. The computer we want to access acts as the “server”, and the rest of the devices that connect to it are the “clients”. When this functionality is enabled, a port is “opened” on the server, which is commonly the number 3389. Ports can be understood as the input and output paths for information to the Internet. If a communication is not made on the correct port, it will be denied. In addition, the router that gives the server access to the Internet must be configured to accept connections to the remote desktop from outside the internal network. The latter will not be necessary if we use a VPN solution to encrypt communications between the client and server computers.
Risks of using remote desktop
Windows remote desktop or RDP, in addition to being used daily for businesses, is a target for cybercriminals, and can become a major risk for organizations that have it enabled if they do not have sufficient security measures. It is very often used to infect with ransomware, malware that encrypts files and demands a ransom.
How do cybercriminals attack RDP?
Sophos has recently published a study after analyzing for a month the attacks suffered by RDP servers accessible from the Internet. In this study, 10 devices (honeypots) with RDP enabled by default, located in different geographical areas, were used as decoys. These are some notable data that can be obtained from the study and that reflect the interest that this type of service presents for cybercriminals:
- 4.3 million fraudulent login attempts were recorded in a 30-day period.
- The first attack occurred just 1 minute and 20 seconds after the honeypots were made public on the Internet.
- All honeypots were attacked within 15 hours of their publication.
- The main usernames attacked were the default usernames of operating systems, such as administrator, admin, user or ssm-user used in AWS (Amazon Web Services).
- Both unprivileged users and administrators were attacked.
- Most of the attacks focused on weak passwords.
The study shows that cybercriminals use brute force attacks, which consist of testing multiple access credentials, i.e. username and password, in an automated manner against targets. If they gain access, they move on to the next target, which is usually to install malware.
In addition to brute force attacks, another attack vector that cybercriminals can use is discovered, unpatched vulnerabilities. Last May, at Protege tu Empresa, we published a warning about a critical vulnerability in the Windows remote desktop that affects older, but still widely used versions, such as Windows 7 or Windows Server 2008, and that allows the attacker to install malware without the user noticing. Despite not being an attack vector as widely used as brute force, these vulnerabilities pose a significant risk if they are not properly patched.
What is the objective of cybercriminals?
Once cybercriminals gain access to the victim’s computer, their main objective is to install malware, which can be of various types:
- Ransomware, malware that encrypts information and demands a ransom. This type of threat has gone from spreading via email with social engineering to doing so through vulnerable RDP services.
- Cryptojacking, which consists of using system resources to mine cryptocurrencies. Cryptocurrency mining has displaced ransomware as the most common and profitable threat.
- Malware that steals confidential information and data, such as passwords to access other services.
- Infections that turn your computer into a zombie, controlled remotely by cybercriminals, forming part of a botnet.
Why do cybercriminals attack it?
Cybercriminals target this service for several reasons:
There are a large number of potentially vulnerable devices. Using specific search engines, such as Shodan, which allows you to perform searches by applying different filters to identify devices connected to the Internet, we can get an idea of the global number of computers with RDP services open on the Internet. This considerably increases the chances that one of them is vulnerable due to having weak passwords, default passwords or not being patched.
To perform the following search in Shodan, the “port” filter has been used, indicating the one usually used in RDP servers, 3389.
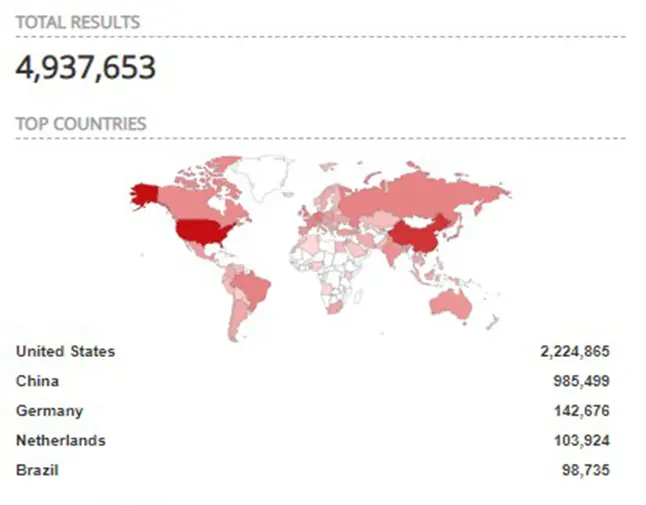
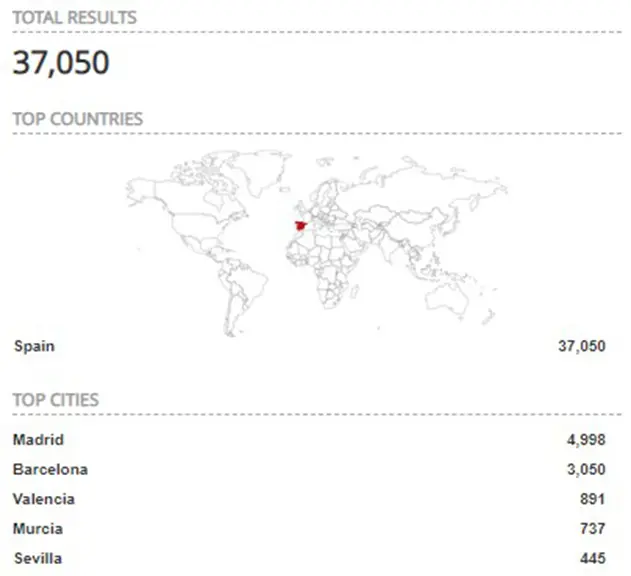
The following search focuses exclusively on RDP servers open to the Internet, but located exclusively in Spain. To do this, the “country” filter and its corresponding value that identifies Spain “ES” will be used.
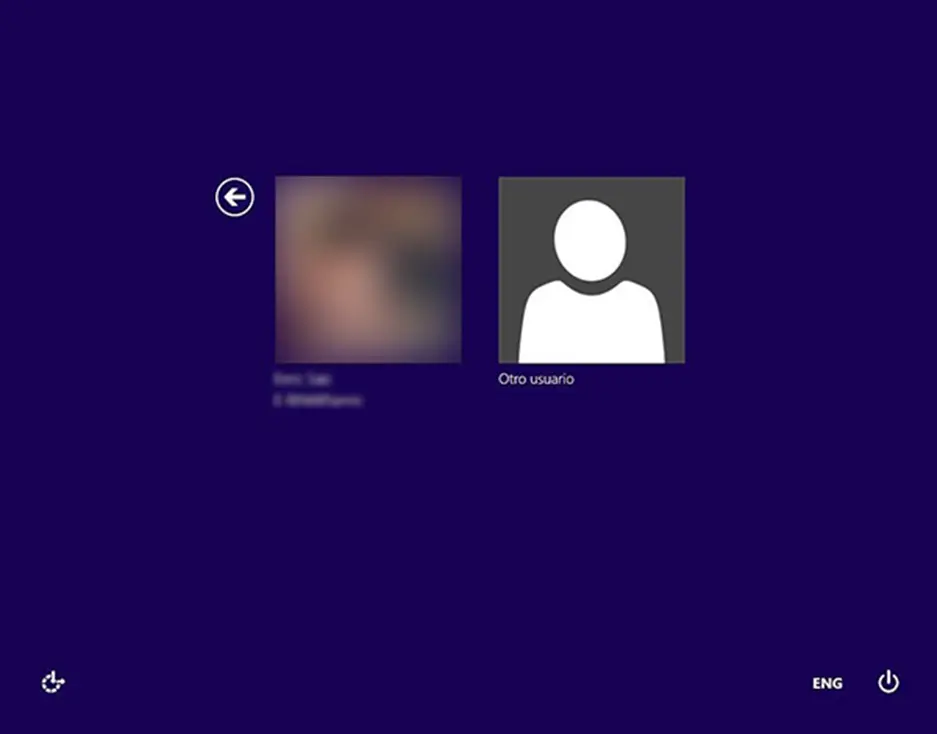
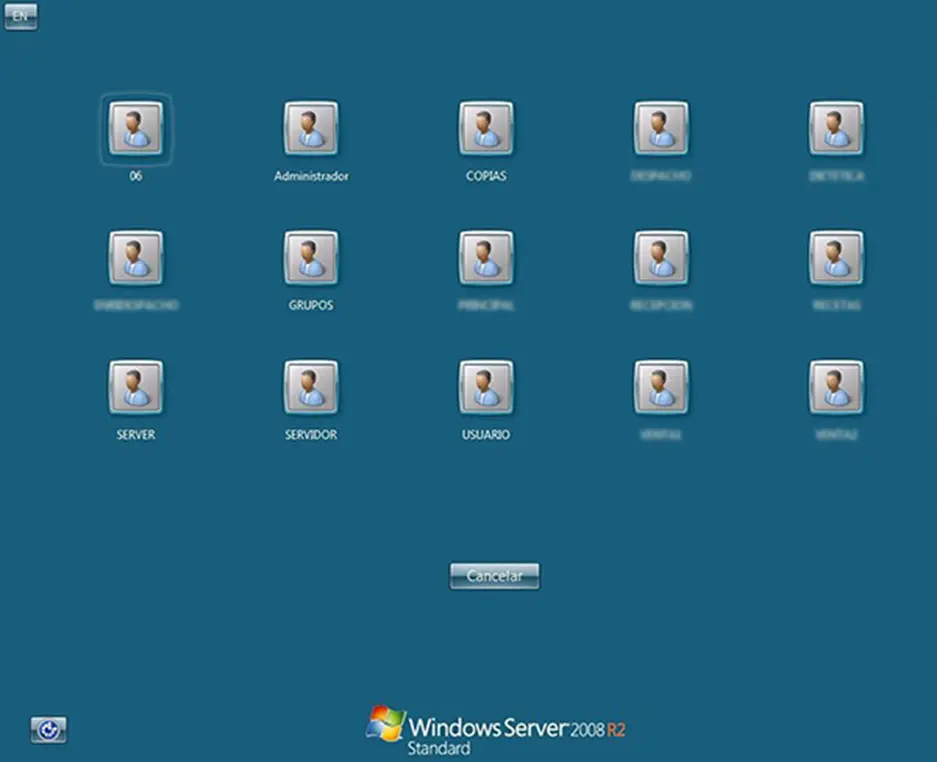
Shodan also shows screenshots of remote desktop servers, which in itself can be considered an information leak that a cybercriminal could use for future attacks.
The possibility of automating attacks. Cybercriminals use specific tools with which they can test multiple users and passwords on multiple victims. In addition, they can use the computational power of the botnet to have a greater chance of success.
Security recommendations for remote desktop
The first thing to consider is whether it is really necessary to use a remote desktop in the company, since any public service on the Internet represents an added risk to the company’s cybersecurity. If it is not necessary, it is advisable to disable the remote desktop service. To do this, it is advisable to contact the technical service or the network administrator.
If it is necessary for the company’s work, these considerations must be taken into account so that its use represents the least possible risk.
Updated systems
The first security aspect in any system is that all software used must be updated to the latest available version. Thus, public vulnerabilities cannot be used to attack the organization.
As already indicated in the previous notice, there are still devices whose life cycle has ended, such as Windows XP or Windows Server 2008, or some such as Windows 7 that are about to end. You should avoid using operating systems without support even if they continue to receive security patches for vulnerabilities as critical as the previous one.
Virtual Private Networks
Using virtual private networks or VPNs as a gateway between the RDP server and the user will minimize the risk of a security incident. A VPN creates an encrypted connection between both devices, thus significantly increasing the privacy of communications. As with all other software, the VPN server must be updated to the latest version.
This is the option that offers the most security guarantees when you have to access a computer in the organization via remote desktop over the Internet.
Using the VPN plus remote desktop combination will increase the level of security, since there is a double barrier to company information. If cybercriminals gain access via the VPN server, they would still have to access the remote desktop.
Strong usernames and passwords
As shown in the study on attacks on remote desktops on the Internet, many are done using generic usernames such as Administrator, so usernames that are not common must be used. This will make it more difficult for brute force attacks to be successful.
Furthermore, it is common for attacks to use weak passwords, so using a strong password that is as long as possible will greatly reduce the chance of unauthorized access. Non-generic usernames and strong passwords should be used for both VPN server and remote desktop access.
Account lockout
Brute force attacks work by trying possible usernames and passwords until they gain access or decide to abandon the attack in search of another target. It is recommended to apply a security policy that restricts user access for a certain time after several unsuccessful attempts. The lockout time will increase depending on the number of unsuccessful attempts, even completely blocking the attacked user.
Two-factor authentication
Using a two-factor authentication system to access the remote desktop will provide an extra plus of security to the organization. To do this, in addition to having to know the username/password pair, it will be mandatory to know a third piece of information (fingerprint, code generated at the time, etc.). Specific applications will preferably be used as a two-factor authentication mechanism instead of SMS messages, since these are more vulnerable to attacks.
Changing the default RDP port
If a VPN solution is not used to access the remote desktop, it is recommended to change the port used by default to connect. The connection to the Windows Remote Desktop service is made through port 3389. Changing this to a different port will make automated attacks by cybercriminals more difficult. This is known as security through obscurity.
Access lists using NLA
Probably not all company users should have access to the remote desktop, so this should be limited to those strictly necessary. By limiting the number of possible users with access, the risk of a cybercriminal gaining fraudulent access is reduced. To do this, it is advisable to use NLA, which stands for Network Level Authentication. Using this technology, users must authenticate themselves on the company network before being able to do so on the RDP server. NLA adds an extra layer of security against possible attacks since double authentication is required. In any case, we must keep the list of enabled accesses updated, without forgetting to supervise and monitor remote access.
Firewall rules
In the company’s firewall, it is also recommended to create specific rules to restrict access to the remote desktop server to a controlled subset of machines. This filtering can be done with IP addresses, allowing access to those associated with the company’s computers.
Using a remote desktop system can be a great help when performing daily work functions, but it can also be a gateway for cybercriminals. Protecting your access by implementing security measures and policies will be vital to avoid becoming a victim of a security incident.
